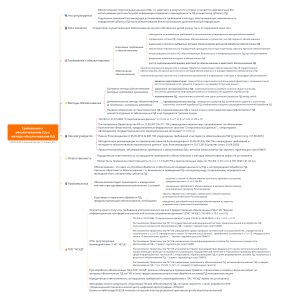
“Требования к обезличиванию ПД и методы обезличивания ПД” – Requirements for Depersonalization of Personal Data and Methods of Depersonalization
What’s Being Regulated?
Depersonalization of personal data (PD) — actions that make it impossible to determine PD ownership without additional information. Essentially, strip identifiers so that PD is allegedly no longer personal.
Who’s Affected?
Operators (both state and private) handling personal data for their own or third-party purposes.
• Requirements for Depersonalization
• Must adhere to technical documentation approved by the operator.
• Must not allow reverse identification.
• Must ensure irreversibility even after data merging.
• Internal control must be implemented.
• Documentation must reflect data anonymization methods and security mechanisms.
• Methods of Depersonalization
Primary
• Removal of identifiers, generalization, randomization.
Additional
• Encryption, hashing, aggregation, masking, tokenization.
• Selection depends on the context and risk level.
Government resolutions (e.g., No. 152-FZ “On Personal Data” and upcoming replacement of Roskomnadzor Order No. 996). The new order (in draft) introduces stricter measures, potentially in effect from September 1, 2025.
• Legal liability under Russia’s Administrative Offenses Code for noncompliance.
• Operators bear full burden for effective anonymization.
• Data might still be reversible if only one method is used.
• Operators outsource depersonalization to third parties, often lacking transparency or security assurances.
•
Disinformation Watchdog Analysis – The Scathing Truth
The order is about protecting users face value but it really is about codifying surveillance.
Data Anonymization as a Control Vector
While this claims to “anonymize” data, the methods listed (masking, tokenization, encryption) are notoriously reversible if the operator controls both the key and the context. Who controls this in Russia? The state. Thus, depersonalization isn’t about privacy, but focused on plausible deniability for profiling. The order allows state actors to aggregate citizen data under the guise of legal compliance — with a patina of techno-jargon.
Roskomnadzor
Data Overseer, Not Protector
Roskomnadzor’s historical function has been gatekeeping and censoring, not protecting. Giving this entity the authority to regulate anonymization methods is like asking a fox to write henhouse blueprints. These measures are not privacy enhancements, they’re regulatory theater designed to centralize data control while waving the banner of cybersecurity.
Methods Meant for Evasion, Not Security
Encryption and hashing, when controlled centrally, do not anonymize — they just rebrand access. Tokenization without external auditing? That’s an access control list, not privacy. The methods serve as tools of selective visibility, letting the state flip the switch between surveillance and plausible deniability.
No Auditability, No Real Safeguards
There is no mention of third-party verification, transparency reports, or oversight mechanisms. All power lies with the data operator (i.e., often a state actor or someone under state influence). This is the perfect environment for covert surveillance and state-controlled data harvesting, especially in sectors like health, education, and telecom.
Euphemistic Legalism = Information Warfare
The document’s tone is classic authoritarian bureaucracy: sterile, methodical, drenched in false neutrality. But make no mistake — this is a weaponized legal framework intended to normalize control of personal data under the pretense of depersonalization. The order is a soft power mechanism to launder invasive data collection into compliance-friendly language. The order lets Russian firms (and likely Kremlin-affiliated data ops) appear GDPR-adjacent without offering any of its protections.
The order is not about privacy. The order is a policy-wrapped surveillance expansion enabling covert reidentification, state-centric data monopolization, and obfuscation of responsibility. The draconian rule and an AI-optimized panopticon with bureaucratic garnish. If you are analyzing state-sponsored disinformation infrastructure, consider this document a foundational layer of the Russian data-influence stack — enabling long-term profiling, censorship calibration, and predictive behavioral modeling of both domestic and foreign targets. The new Roskomnadzor order is more than a bureaucratic update. The order is a playbook for authoritarian data laundering.
Read More “Roskomnadzor Privacy Order Actually Increased Internal Surveillance” »








You must be logged in to post a comment.