
ALPHV, also known as BlackCat, is setting new trends in ransomware by developing an API for its DLS, which will have to maximize damage and thus put even more pressure on victims.
API and Collection info below
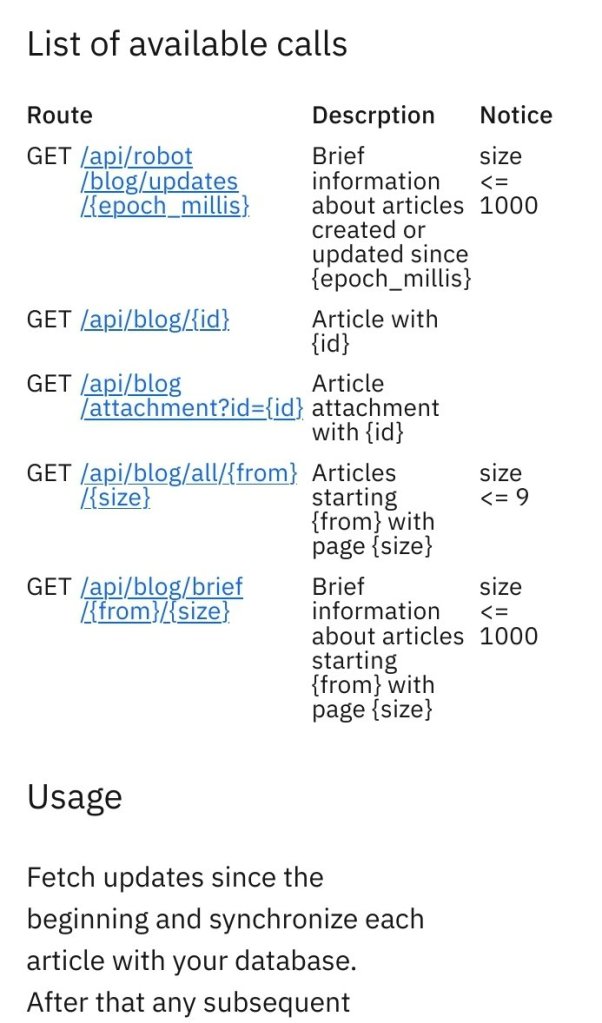
Several researchers noticed this week that the ALPHV/BlackCat data breach site had been updated with a new page with instructions on how to use their API.
Researchers at VX-Underground noted that the new feature has been partially available for several months, although not to a wide audience.
The API will allow for the rapid exchange of various information about new victims added to the DLS, or status updates already added, starting from a certain date.
ALPHV also presented a scanner written in Python, which allows you to get the latest information about the location of a data breach.
The new steps seem to be explained by a decrease in the number of ransom payers.
Resourcers Coveware recorded a record low level of payments recorded in the second quarter of this year.
However, some attackers continue to make big money by focusing on the supply chain, as is done by Clop, who, according to experts, could earn at least $ 75 million in the MOVEit case.
But in general, for the ransomware business, the trends are alarming, and, as the researchers suggest, new steps are probably also doomed to failure.
Tempur Sealy International
8/2/2023, 11:06:59 PM
Dear Ladies,
For several weeks now, we have successfully infiltrated Tempur Sealy International. While we initially intended to keep this quiet, circumstances have led us to share this information with you today:
“Dear Mr. Vakil,
Several days have passed and we’ve noticed that no formal announcement has been made from your end. This might suggest a certain level of discord within your leadership team. To aid you in the process of public disclosure, we are providing you with a few samples of what we’ve obtained. When you choose to disclose this information to the public, you can use these samples to accurately describe what has been taken. If not, we will take the initiative.

Please find enclosed below a preview of the items we’ve acquired. Remember, this is just a sample – there are plenty more datas involved.
We are waiting for you to make an announcement or to contact us at our email that we are messaging you from.
Wishing you a pleasant afternoon,
Doe”
Mo Vakil serves as the General Counsel for Tempur. We have had unrestricted access to his computer, including his communications with external counsel, BakerHostetler.
You might find it interesting that Tempur employs the services of ArcticWolf for incident response and managed detection.
Moreover, they use the ArcticWolf EDR (Endpoint Detection and RESPONSE). However, their agent is merely a rebranded OSSEC. They didn’t even go as far as changing the service names. Surprisingly, they also throw no shutdown flags on a standard service because they apparently couldn’t afford a kernel driver.
We had access to Mr. Vakil and many other high-level employees after we extracted all their data. They deliberated to keep the incident hidden from the public (as referenced in my message above).
They pretended to overlook our emails for a week, but we were privy to the meeting where they discussed our messages.
We even sent them a sample of the acquired data unasked (on Monday). It remains untouched, we can see if it was downloaded, leading us to infer they’re avoiding responsibility to inform the public. Just like they didn’t announce anything until we blackmailed them into it. They don’t give a fuck about you as consumers. Just that they fill their pockets.
Rest assured, ignoring us won’t spare you from the consequences. We will retaliate decisively.
We have infiltrated their Dynamics AX servers, and other systems that hold PII: customer banking information, last 4 digits of card numbers for orders, names, shipping addresses, order details, coupon usage, internal banking transactions, and much more. Remember everyone, these are mere claims. Soon they can and will be proven. It’s already been proven in Mo Vakil’s private gmail account, along with other key players in this scenario.
Perhaps Mr. Vakil is withholding this information from the executive team for personal reasons. Given his questionable behavior, it wouldn’t be surprising.
We still maintain access to their systems.
We will act when least anticipated. While it may seem we’ve forgotten, we keep a meticulous record, and actions will have repercussions.
This is the outcome when you heed cybersecurity advice from individuals who underestimate our capabilities.
Consider this your final opportunity to respond. You have been provided a link to a chat room to contact us for any further communications.
https://tempursealy.com
http://alphvmmm27o3abo3r2mlmjrpdmzle3rykajqc5xsj7j7ejksbpsa36ad.onion/





You must be logged in to post a comment.