Executive Analytic Brief
Russian statecraft has metastasized into a “mobilization state” model in which the distinction between public institutions and private entities has effectively dissolved. Intelligence analysis, now corroborated by the Treadstone 71 assessment on Cognitive Warfare and the Hybrid CoE Paper 27, confirms that the Kremlin orchestrates a vast ecosystem of Non-State Actors (NSAs) to project power globally. A critical new finding is the weaponization of “nuclear fear” by these actors—specifically cyber groups and media proxies—to induce cognitive paralysis in Western decision-making. Moscow utilizes these actors not merely for deniability, but as essential force multipliers to bridge the chasm between its maximalist geopolitical ambitions and its materially constrained conventional capabilities.
Russia operationalizes Non-State Actors as a cohesive “grey zone” assault force, integrating criminal networks, private industry, and ideological organizations into a unified war economy. Western countermeasures remain reactive because they fail to address the systemic fusion of these actors with the Russian state’s new “cognitive warfare” doctrine. Current trends in late 2025 indicate a dangerous maturation of this threat- the emergence of rogue yet-aligned cyber groups like Z-Pentest and Sector 16 targeting US critical infrastructure, the complete consolidation of the Africa Corps in the Sahel, and the systematic use of cyber-proxies to trigger false civil defense alerts.
Primary threat actors comprise a triad of power- the Presidential Administration (PA) provides strategic direction; the intelligence services (FSB, GRU, SVR) execute operational orchestration; and a tiered network of NSAs implements the actions.
- Armed- Africa Corps (formerly Wagner), Redut, Rusich.
- Cyber- State-controlled (Sandworm), Co-opted Criminals (Z-Pentest, Sector 16), Hacktivist Auxiliaries (Cyber Army of Russia Reborn).
- Cognitive/Propaganda- Social Design Agency, Russian Orthodox Church, State Media proxies (Rybar).
- Economic- The shadow fleet, dual-use good smuggling cartels.
Moscow employs these actors to conduct kinetic sabotage against European logistics, destructive cyber campaigns targeting operational technology (OT), and high-intensity “fear operations” designed to simulate nuclear escalation. The operational model has shifted from loose delegation to “orchestrated chaos.” Operations in late 2025 focus on degrading Western critical infrastructure (water/energy), fracturing NATO cohesion through nuclear blackmail narratives, and securing resource extraction in the Global South to finance the war.
The proliferation of state-linked NSAs fundamentally challenges Western legal frameworks and military escalation ladders. Russia imposes strategic costs without triggering Article 5 by using actors that fall short of the threshold for armed conflict. The integration of “nuclear fear” operations—such as hacking air raid sirens to broadcast false nuclear alerts—demonstrates a willingness to target the psychological resilience of civilian populations directly, risking accidental escalation through panic.
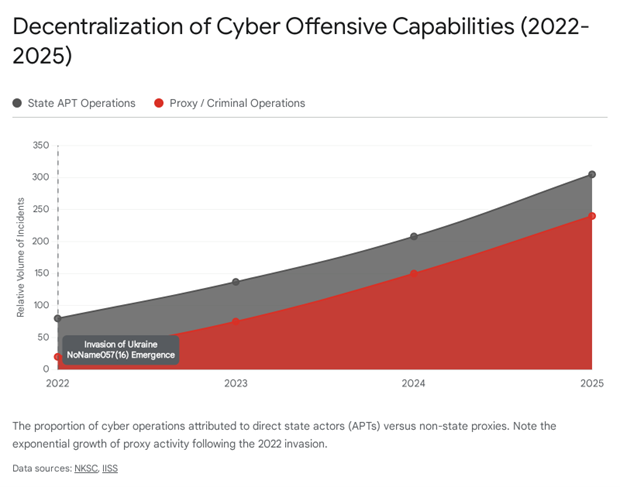
Intelligence analysis is critical at this juncture because Russian NSA activity has entered a volatile “post-Wagner” phase. The emergence of splinter groups like Z-Pentest in 2025, formed due to funding disputes with the GRU, yet still attacking Western targets, signals a shift away from strict state control toward ideological alignment. Simultaneously, the successful weaponization of “nuclear fear” has become a primary doctrine to deter Western aid to Ukraine.
Russian NSAs have destabilized the Sahel, displacing Western influence; disrupted European logistics via kinetic sabotage; and maintained revenue streams through illicit economic networks. Notably, cyber-proxies have successfully breached US municipal water systems and broadcast fake missile alerts in Europe, proving the viability of “cognitive terror” tactics. However, operational failures persist, particularly where command-and-control structures fracture, leading to indiscriminate violence by groups like the Africa Corps that alienates local populations.
Projections for 2026-2030 suggest a deepening of the “crime-terror-state” nexus. Russia will likely aggressively export its “Regime Survival Package” to the Global South. The cyber domain will witness a shift from disruptive DDoS attacks to “Fabricated Emergency” events—cyberattacks designed to trigger mass panic (e.g., simulating a nuclear plant leak) rather than just physical damage.
Intelligence Source Assessment- Credibility, Validity, and Provenance
Document Provenance and Institutional Authority
This assessment synthesizes findings from two primary high-confidence sources. First, Hybrid CoE Paper 27, “Handbook on the Role of Non-State Actors in Russian Hybrid Threats” (Dec 2025), provides the structural taxonomy of the threat.1 The European Centre of Excellence for Countering Hybrid Threats operates as an autonomous, NATO/EU-affiliated organization, ensuring its output reflects a broad Euro-Atlantic security consensus.2
Second, the assessment incorporates the Treadstone 71 report “Russia’s Nuclear Fear Operations and Cognitive Warfare (1986–2025)”.1 Treadstone 71 is a reputable cyber intelligence firm known for adversarial profiling and cognitive warfare analysis. While the Hybrid CoE report provides the structural framework, the Treadstone document provides the doctrinal insight into how these actors weaponize psychology.
Russia’s Nuclear Fear Operations and Cognitive Warfare (1986–2025)
Authorship Analysis and Expertise
The Hybrid CoE team (Dr. Vladimir Rauta, Dr. Magda Long, et al.) brings academic rigor and operational experience in proxy warfare and covert action.3 The Treadstone 71 analysis, likely led by Jeff Bardin, contributes specialized expertise in “cyber-cognitive” operations, specifically detailing how cyber actors are used to amplify psychological terror. This combination enables an analysis of both the physical movements of proxies and the psychological impact of their operations.
Relevance and Timeliness
Both source documents are dated late 2025 and capture critical recent shifts. The analysis accounts for the post-Prigozhin restructuring of Wagner into the Africa Corps 5, the 2025 split of cyber groups like Z-Pentest from the GRU 6, and the intensification of nuclear rhetoric following geopolitical shifts in Scandinavia.1 This timeliness is crucial for understanding the current fragmented yet dangerous state of Russian proxy networks.
Validity of Analytical Frameworks
The “Mobilization State” model used by Hybrid CoE aligns with Treadstone 71’s concept of “Cognitive Warfare.” Both frameworks validate the premise that Russia views the psychological domain as a decisive battlefield. The reports correctly identify that the distinction between “state” and “non-state” is irrelevant in the Russian context; the only relevant metric is “utility to the state.”.1
Potential Bias and Intelligence Gaps
The Hybrid CoE report maintains a Western security focus, framing actions primarily as threats to NATO/EU. The Treadstone document, focusing on “Nuclear Fear,” may emphasize psychological effects over physical capabilities, potentially interpreting incompetence (e.g., accidental leaks) as intentional psychological operations. Intelligence gaps remain regarding the precise financial mechanisms linking the new “Africa Corps” to the Russian state budget and the exact chain of command for splinter cyber groups like Sector 16.
The Strategic Logic- The Mobilization State and Cognitive Warfare
The “Grey Zone” and Cognitive Imperative
Russia operates within a strategic paradox- maximalist ambitions constrained by limited conventional power. NSAs resolve this by operating in the “grey zone.” However, new intelligence clarifies that the ultimate goal of these operations is not just physical disruption, but Cognitive Paralysis 1
Strategic logic relies on three pillars-
- Plausible Deniability & Attribution Fatigue- The Kremlin employs NSAs to create ambiguity. Even when attribution is highly probable (“implausible deniability”), the sheer volume of attacks by diverse actors—from hacktivists to privateers—creates “attribution fatigue” in Western capitals, delaying decisive response.1
- Cognitive Warfare (Reflexive Control)- Drawing from Soviet “reflexive control” theory, Russia uses NSAs to shape an adversary’s perceptions to induce voluntary self-restraint. The weaponization of “nuclear fear” via media proxies and cyber-simulations is the primary application of this doctrine in 2025. The goal is to force Western populations to “self-deter” from supporting Ukraine due to fear of escalation.1
- The Mobilization State- Neutrality is impossible. Oligarchs, criminals, and tech companies are coerced into supporting the war effort. This conversion of the private sector into a “reservoir of auxiliaries” allows the state to surge capabilities without budgetary expansion.1
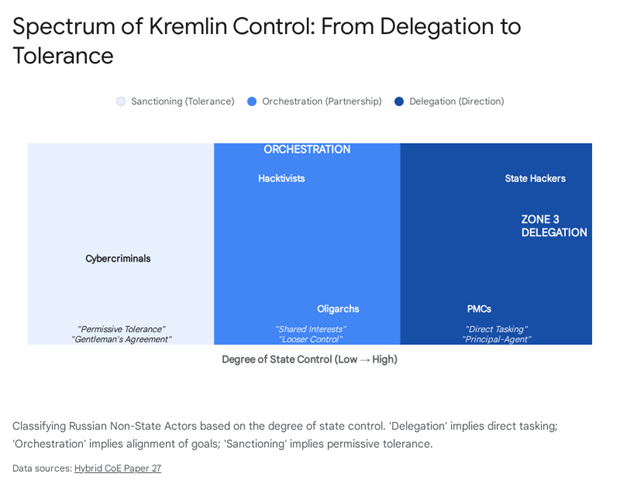
The Evolution of State-NSA Relations
The relationship between the Kremlin and these actors operates on a spectrum from Delegation to Orchestration and Sanctioning.
Recent intelligence on cyber groups like Z-Pentest indicates a fraying of “Delegation.” These groups, dissatisfied with GRU funding, have moved toward “Orchestration” or even “Sanctioning,” conducting attacks that align with state goals but are funded by independent criminal extortion.6 This suggests a dangerous trend- the “democratization” of hybrid warfare, where state-aligned actors operate with increasing autonomy and unpredictability.
Deep Dive- Armed Non-State Actors (ANSAs)
The Post-Wagner Transformation- Rise of the Africa Corps
By mid-2025, the Russian Ministry of Defence (MoD) successfully transitioned the Wagner Group’s operations in the Sahel into the state-controlled Africa Corps.5 This entity now operates directly under the GRU, removing the corporate autonomy Prigozhin previously enjoyed.
Operational analysis confirms the Africa Corps has entirely subsumed Wagner in Mali, Burkina Faso, and Niger. Unlike Wagner’s frontline shock troops, the Africa Corps focuses on regime protection and training, though they remain implicated in severe atrocities. Reports from late 2025 confirm that Africa Corps personnel have committed rapes and beheadings in Mali, using terror as a tool of population control. This brutality serves a strategic function- displacing Western influence by offering ruthless regime security packages that Western powers cannot legally or morally match.
The Ecosystem of Violence
Private Military Companies (PMCs)- Redut remains the MoD’s primary recruitment vehicle for the war in Ukraine, functioning as a “shadow army” that bypasses mobilization laws.1
Paramilitary Formations- Ideological groups like Rusich and the Russian Imperial Movement (RIM) provide specialized violence. Intelligence links RIM to the “Partisan” training program, which radicalizes Western white supremacists, creating a potential “fifth column” of domestic terrorists within NATO states.6
Criminal Auxiliaries- Transnational Criminal Networks (TCNs) provide logistics and “wetwork.” The 2024 UK investigation Operation Destabilise revealed that TCNs provide “black cash” for intelligence operations, creating a self-sustaining loop where drug trafficking funds political subversion 7
Deep Dive- Cyber Non-State Actors (CNSAs)
From Cybercrime to Cognitive Terror
The cyber domain has seen the most rapid evolution in 2025. The distinction between “hacktivist” and “state asset” has collapsed. A new breed of actor has emerged- the Cognitive-Cyber Proxy. These groups do not just disrupt systems; they attack the psychology of the target population.
The Actor Typology & 2025 Shifts
State-Controlled Groups (APTs)- Sandworm (GRU) remains the apex predator, coordinating attacks with kinetic missile strikes.
The “Rogue” Splinters (Z-Pentest & Sector 16) – In late 2024, administrators from the Cyber Army of Russia Reborn (CARR) splintered over funding disputes with the GRU, forming Z-Pentest and Sector 16. By Jan 2025, they allied with a new group, Sector 16. These groups aggressively target US and EU critical infrastructure (OT/ICS), specifically energy and water sectors in Texas and Europe. Their motivation is a hybrid of ideology and extortion, making them harder to deter via diplomatic channels.
Hacktivist Auxiliaries (CARR)- The Cyber Army of Russia Reborn remains active but has pivoted toward “Fear Operations.” Intelligence confirms CARR was responsible for breaching US municipal water systems and, crucially, hacking media outlets to broadcast fake air raid and nuclear alerts.
Emerging Threat- Fabricated Emergencies
The specific hacking of alerting systems represents a qualitative leap in hybrid warfare. By triggering air raid sirens or broadcasting fake “Nuclear Strike Imminent” messages, groups like CARR directly support the Kremlin’s “Nuclear Fear” doctrine.1 The intent is to normalize panic and erode trust in public warning systems, effectively “numbing” the population to real threats.
Deep Dive- Propaganda and Disinformation NSAs (PDNSAs)
The Architecture of “Nuclear Fear”
Russian information operations are now fully integrated with “Cognitive Warfare” objectives. The primary narrative payload in 2025 is Nuclear Fear.
State Media Proxies- Figures like Vladimir Solovyov and military blogs like Rybar (which has grown to 1.3 million subscribers) are tasked with normalizing the idea of limited nuclear use. Rybar acts as a “grey” intelligence outlet, publishing coordinates of Ukrainian positions while simultaneously pushing narratives about Western “nuclear provocations” to justify Russian escalation.
The Social Design Agency (SDA) continues to run the Doppelganger campaign, cloning Western media to inject these fear narratives directly into the newsfeeds of European citizens. The SDA’s operations are now viewed by the Kremlin as a “state-sanctioned information war,” utilizing leak-based narratives to fracture NATO resolve.
The “Global South” Pivot
PDNSAs have aggressively pivoted to the Global South. Networks like TV BRICS and local influencers in Africa promote Russia as an anti-colonial partner. The networks are not just PR; they are operational preparation of the environment (OPE) to secure the Africa Corps’ presence and mining contracts.8
Deep Dive- Social and Political NSAs (SPNSAs)
The Orthodox Nexus & “Nuclear Orthodoxy”
The Russian Orthodox Church (ROC) has become a central pillar of the “Cognitive Warfare” apparatus. Patriarch Kirill’s framing of the war as a “metaphysical battle” provides the moral permission structure for nuclear rhetoric. The church actively “sanctifies” nuclear weapons, merging religious salvation with atomic destruction in a doctrine of “Nuclear Orthodoxy”.1 In the Balkans, the ROC and Serbian Orthodox Church (SOC) function as influence nodes, promoting pan-Slavic nationalism to destabilize Montenegro and Bosnia.1
Compatriot Organizations
Entities like Pravfond continue to use “lawfare” to challenge Western sanctions and protect Russian assets, effectively weaponizing Western legal systems against themselves. These groups provide cover for intelligence officers operating under diplomatic or NGO status 1
Deep Dive- Economic and Financial NSAs (EFNSAs)
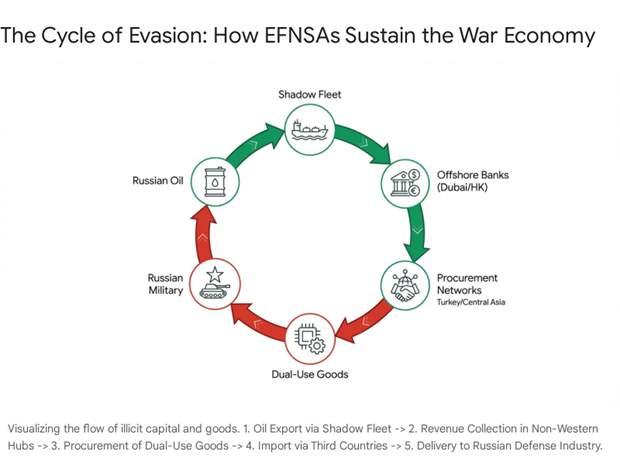
The Shadow Fleet & Evasion Enablers
The “Shadow Fleet” of uninsured tankers now transports over 4 million barrels of Russian crude daily, bypassing the G7 price cap.9 This is the financial lung of the war effort.
Oligarchs as State Custodians- Post-2022, oligarchs function as “state bankers,” required to finance PMC operations and “grey imports” of microchips. The Treadstone analysis highlights how illicit financial flows are increasingly used to fund “active measures” directly, bypassing official state budgets to avoid attribution.1
Orchestration- The Command and Control of Chaos
The Hybrid Control Network
The “Vertical of Power” managing these NSAs is distinct-
- Presidential Administration (PA) – Sergey Kiriyenko (First Deputy Chief of Staff) serves as the “Curator,” setting strategic narratives (e.g., “Nuclear Fear”) and allocating budgets to PR firms like SDA.
- GRU (Military Intelligence)- Directly commands the Africa Corps, directs Sandworm, and loosely manages/funds hacktivist groups like CARR. However, friction over funding has led to the splintering of groups like Z-Pentest.6
- FSB (Federal Security Service)- Manages the ROC, Oligarch networks, and the “criminal-intelligence” nexus used for sanctions evasion and assassinations.
Fragmentation Risks
The 2025 splintering of cyber groups exposes a flaw in this model- Principal-Agent Drift. As the Kremlin outsources more violence to criminal and ideological groups, it loses granular control. Z-Pentest’s independent attacks on US infrastructure, driven by profit or fanaticism rather than direct orders, risk triggering an escalation Moscow may not have intended.6
Strategic Foresight- Outlook 2026-2030
Scenario Analysis
The “Cognitive-Kinetic” Convergence (High Probability)- Russia will combine cyberattacks on civil defense systems (air raid sirens, SMS alerts) with deepfake media to create Fabricated Nuclear Emergencies. The goal is to trigger mass panic and paralysis in a NATO capital without firing a shot.1 The CARR and Sector 16 attacks in 2025 are dress rehearsals for this scenario.
The “Crimintern” Consolidation (Medium Probability)- The integration of TCNs into statecraft deepens. Russian intelligence effectively franchises sabotage operations to local gangs across Europe, creating a steady drumbeat of low-level arson and disruption that is difficult to attribute or deter.7
The Global South Fortress (Medium Probability)- The Africa Corps succeeds in carving out a “resource corridor” across the Sahel, funded by gold and protected by regime security deals, insulating the Russian war machine from Western sanctions by creating an autarkic economic bloc with rogue regimes.10
Conclusions and Recommendations
The integration of Hybrid CoE and Treadstone 71 intelligence confirms that Russia has moved beyond “hybrid warfare” to “Cognitive Warfare.” The ultimate target of the diverse NSA ecosystem—from the Africa Corps to Z-Pentest—is the West’s psychological resilience. The weaponization of “nuclear fear” is not a bluff but a calculated operational line of effort designed to induce self-deterrence.
Recommendations for Policymakers
- Cognitive Resilience- NATO must treat “Fear Operations” (e.g., fake nuclear alerts) as equivalent to kinetic strikes. Public warning systems must be hardened against cyber-intrusion to prevent induced panic.
- Target the “Grey” Proxies- Sanctions and cyber-offensive operations must aggressively target the “splinter” groups like Sector 16 and Z-Pentest. Their lack of complete state protection makes them vulnerable to disruption.
- Expose the “Nuclear Orthodoxy”- Counter-messaging should highlight the cynical weaponization of the Church and the “nuclear blackmail” narrative to delegitimize it in the Global South and among religious communities.
Russian statecraft has transcended traditional hybrid warfare, evolving into a total cognitive assault where the target is not infrastructure, but the psychological resilience of the adversary. Moscow’s orchestration of a diverse, often volatile ecosystem of proxies—ranging from the brutal Africa Corps to the reckless cyber-extortionists of Sector 16—demonstrates a willingness to gamble with escalation to achieve strategic paralysis. “Nuclear fear” and fabricated emergencies serve as the primary munitions in this campaign, designed to force Western capitulation through induced panic rather than military defeat. Security paradigms must shift immediately from passive observation of the “grey zone” to active disruption of the financial, technical, and narrative lifelines sustaining these non-state actors. Victory in 2026 and beyond requires stripping the Kremlin of its deniability and inoculating democratic societies against the weaponization of their own anxieties.
Works cited
- Hybrid-CoE-Paper-27-Handbook-on-the-role-of-non-state-actors-in-Russian-hybrid-threats.pdf
- Hybrid CoE – Hybrid CoE – The European Centre of Excellence for Countering Hybrid Threats, accessed December 21, 2025, https-//www.hybridcoe.fi/
- Vladimir Rauta – War by Proxy – University of Reading, accessed December 21, 2025, https-//www.reading.ac.uk/politics-international-relations/stories/vladimir-rauta
- Dr Magda Long – King’s College London, accessed December 21, 2025, https-//www.kcl.ac.uk/people/magda-long
- Africa Corps (Russia) – Wikipedia, accessed December 21, 2025, https-//en.wikipedia.org/wiki/Africa_Corps_(Russia)
- Pro-Russia Hacktivists Conduct Opportunistic Attacks Against US and Global Critical Infrastructure | CISA, accessed December 21, 2025, https-//www.cisa.gov/news-events/cybersecurity-advisories/aa25-343a
- Russia, Ukraine, and organized crime and illicit economies in 2024 – Brookings Institution, accessed December 21, 2025, https-//www.brookings.edu/articles/russia-ukraine-and-organized-crime-and-illicit-economies-in-2024/
- Russia Futures – Stimson Center, accessed December 21, 2025, https-//www.stimson.org/2025/russia-futures/
- Andis Kudors | Fulbright Scholar Program, accessed December 21, 2025, https-//fulbrightscholars.org/grantee/andis-kudors
- Russia’s Africa Corps- Wagner’s Successor in Africa (2022–2025) – Robert Lansing Institute, accessed December 21, 2025, https-//lansinginstitute.org/2025/09/30/russias-africa-corps-wagners-successor-in-africa-2022-2025/