A sophisticated fraud operation actively targets individuals and businesses immediately following their trademark submissions to the United States Patent and Trademark Office (USPTO). The operation demonstrates a clear understanding of the trademark application process, exploiting the Applicant’s anxiety and the inherent complexities of bureaucratic procedures. An intelligence analysis of the group’s methods reveals a structured, multi-stage campaign designed for social engineering and financial extraction.
Advanced Impersonation and Targeting
The new information reveals a significant evolution in the threat actor’s tradecraft. Their operation is not based on generic, invented personas but on the specific, targeted impersonation of real, verifiable officials within the United States Patent and Trademark Office and the legal community.
The use of Cynthia Tripi’s name, a genuine USPTO Managing Attorney, is a sophisticated choice. It allows the fraudulent communication to withstand initial scrutiny. A cautious applicant who searches for the name will find a legitimate USPTO employee, creating a powerful—and false—sense of security. This moves the tactic from simple impersonation to calculated identity theft for the purpose of fraud. Similarly, using the name of a real lawyer, Michael Clark, adds another layer of credibility to the scheme.
Furthermore, the connection to high-volume, low-cost filing websites like PayAfterTM and Trademark Engine suggests a specific targeting methodology. These platforms attract a large volume of first-time or cost-sensitive applicants who are often navigating the complex trademark process without professional legal counsel. This demographic is the ideal target for the scam. The applicants are already conditioned to interact with the trademark process through online, non-traditional channels, and they are more susceptible to confusion regarding official procedures and fees. The threat actors are likely exploiting the public data generated by these filings, knowing they have a target-rich environment of applicants who are less likely to have a lawyer to consult.
The perpetrators are a coordinated group, as indicated by their shared infrastructure and consistent methodology. Information suggests the operators are based in India but mask their location through Voice over IP (VoIP) phone numbers with U.S. area codes, such as the 571 Virginia code common for the D.C. metro area, where the USPTO is headquartered. They adopt common American names to build rapport and disguise their foreign origin. Their corporate entity for processing payments, “Wa Company” or “Wa corporation,” appears to be a disposable shell company, designed to collect funds before being detected and shut down.
The group’s operational pattern, or modus operandi, is replicable and systematic. They monitor the public USPTO Trademark Electronic Application System (TEAS) for new filings. The Applicant’s contact information, a mandatory part of the submission, becomes their targeting data. Within hours or days of a filing, they initiate contact, capitalizing on the period when an applicant is most expectant of official communication. Their proficiency in navigating the USPTO website and referencing specific, albeit misapplied, statutes gives them a veneer of legitimacy that can deceive even cautious applicants.
Deconstruction of Tactics, Techniques, and Procedures (TTPs)
The fraud hinges on expertly crafted social engineering. The emails are the primary tool for initiating contact and establishing a pretext.
Impersonation and Pretexting: The scammers directly impersonate USPTO officials, from an “Assistant to the Examining Attorney” to the office itself. The provided emails are masterful examples of pretexting—creating a believable scenario to manipulate a target. The first email invents a “Classification Review Notice,” a plausible but non-standard communication. It cites legitimate sections of the Trademark Manual of Examining Procedure (TMEP) and U.S. Code, adding a layer of authenticity. The second email fabricates an issue with the “identification of goods/services,” another common and confusing part of the application process. Both pretexts are designed to address genuine points of applicant uncertainty.
Authority and Urgency: The communications are saturated with language of authority. Phrases like “Pursuant to 15 U.S.C.,” “Action Required,” and “Failure to comply may result in…delays” are intended to intimidate the Applicant into immediate action. The scammers create a false sense of urgency by setting tight, arbitrary deadlines, such as “Before 6:00 PM PST today,” or scheduling a mandatory consultation just two days away. This tactic short-circuits the victim’s decision-making process, pressuring them to call the provided number rather than independently verify the communication through official channels.
Channeling and Isolation: The scheme carefully controls the communication environment. The emails explicitly direct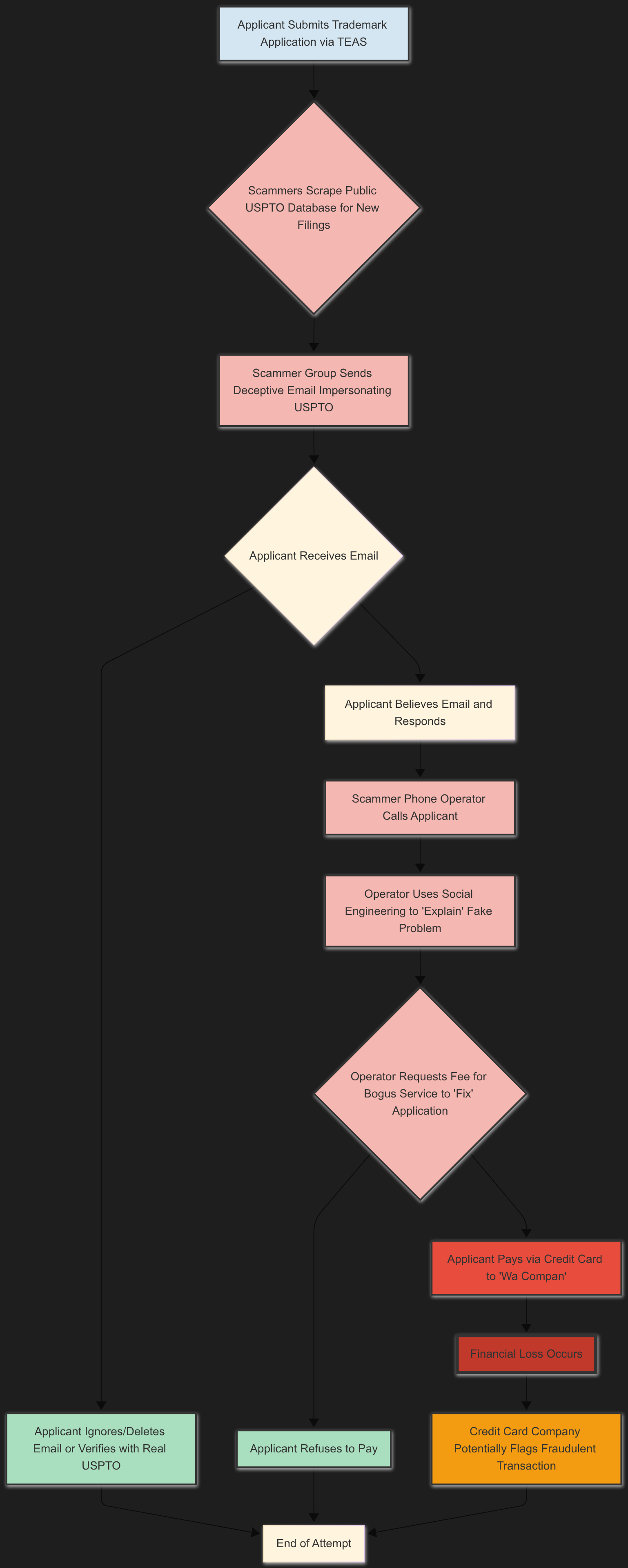
Call-Handling Tradecraft
The sequence of events described in the sample below—calling one number, leaving a message, and receiving a near-instantaneous email redirecting you to a different person and number—is a deliberate and sophisticated procedure.
This tradecraft reveals a structured, multi-layered operational model. The initial phone number for “Elijah Jackson” functions as a screening mechanism or a “dead drop.” It is likely an unmonitored voicemail box designed solely to capture responses from engaged targets. A voicemail left by a potential victim acts as a “tripwire,” triggering an immediate internal alert to the scammer team.
The rapid follow-up email from “Cynthia Tripi” demonstrates that the group actively monitors these tripwires in near real-time. This procedure redirects the engaged target, now identified as a “live lead,” to a second, specific operator—”Michael Clark.” This person is likely one of their more skilled conversationalists or “closers,” tasked with handling high-probability targets.
This multi-persona, multi-channel approach achieves several objectives. First, it enhances their legitimacy; in a real office, it is common for one person to be unavailable and for an assistant to redirect a query. Second, it creates operational efficiency, ensuring their primary operators do not waste time answering calls from security researchers, bots, or uncommitted applicants. Third, it compartmentalizes their operation, making it more difficult to analyze from the outside and protecting their primary phone numbers from being immediately flagged for spam or fraud. The process is designed to filter, qualify, and funnel potential victims to their most effective operatives.
Financial Extraction Tradecraft
The operator, “Michael Clark,” executes the final stage of the deception with a carefully orchestrated script designed to build false confidence before extracting payment.
His methodology cleverly avoids overtly fraudulent actions, such as directing the victim to a fake website. Instead, he weaponizes legitimate USPTO resources against the Applicant. By guiding the victim through the official USPTO website, help pages, and fee structures, he grounds the conversation in reality and positions himself as a helpful authority. He then introduces the fraudulent premise—an urgent, mandatory fee of “$600 per classification code”—and presents it as an official requirement he discovered while “assisting” the victim.
The core of this tradecraft is an “email confirmation gambit” designed to manufacture a dead end and create pressure. The operator provides a plausible but incorrect email address (michaelclark@uspto.gov). The scammer knows the USPTO.gov server, like many large organizations’ servers, may be configured not to send bounce-back or “non-delivery” receipts for non-existent addresses. The victim sends the email and, upon seeing no rejection, assumes the address is valid. When the operator feigns non-receipt and provides a second variation (michael.clark@uspto.gov), which also fails, he creates a pretext of “technical difficulties.”
The manufactured failure is the pivot point of the entire operation. After demonstrating that the “official” channel of email confirmation is not working, the operator presents direct payment over the phone as the only remaining, immediate solution to the urgent problem he created. The solution is a classic confidence trick, using manufactured technical issues to exhaust the victim’s options and pressure them into financial compliance.
Indicators of Fraudulent Communication
A direct comparison between the scammers’ methods and legitimate USPTO procedures reveals clear indicators of fraud. Genuine USPTO examining attorneys communicate through official, non-courtesy “Office Actions” sent from @uspto.gov email addresses. They do not demand immediate phone consultations for routine classification issues or request payments over the phone to third-party corporations.
| Deceptive Element | Scammer’s Implementation | USPTO Reality |
| Point of Contact | A .com email address and a Virginia (571) VoIP number. | Official communication from a @uspto.gov email address. All official documents are posted to the TEAS portal. |
| Communication Type | “Courtesy communication” or “Classification Review Notice.” | Formal, non-optional “Office Action” is the standard for communicating official requirements. |
| Urgency | Fabricated deadlines and immediate consultation demands. | Office Actions provide a multi-month window (typically three to six months) for a formal written response. |
| Resolution Method | A mandatory phone call with a specific “examining attorney.” | Resolution occurs through a formal, written response filed by the Applicant via the TEAS portal. |
| Payment Request | An implied or explicit request for fees to be paid over the phone or online to a third-party like “Wa Compan.” | All official USPTO fees are paid directly to the “U.S. Patent and Trademark Office” through the official TEAS system. |
Analysis of Communication Style and Structure
A combined semiotic, stylometric, and forensic linguistic analysis of the fraudulent emails reveals a deliberate and layered construction. The language is not merely a carrier of information; the language itself is the primary weapon, engineered to elicit a specific psychological and behavioral response from the target.
Semiotic Analysis
Semiotics, the study of signs and symbols, shows how the emails construct an aura of authority. The scammers employ a system of signs to signify legitimacy. The sender name, “United States Patent and Trademark Office,” is the most powerful signifier, immediately establishing an unequal power dynamic. Legal citations, such as “15 U.S.C. §§1051–1052” and “TMEP §§ 1401–1402,” function as symbols of unimpeachable legality. Their specific meaning is irrelevant to the target; their presence alone signifies a complex, official process that the Applicant is unqualified to question. The formal structure—the salutation, numbered lists, and formal closing—mimics the visual grammar of bureaucratic correspondence. Even the modern inclusion of emojis like the phone (📞) and hourglass (⏳) are semiotic choices, signifying a clear call to action and a sense of expiring time in a visually accessible way.
Stylometric Analysis
A stylometric examination of the writing style points to a careful imitation of official communication, but with subtle yet significant deviations. The sentence structure is predominantly declarative, a common feature of bureaucratic writing. The vocabulary, or lexicon, is deliberately formal, employing terms like “pursuant to,” “deficiencies,” and “abandonment” to match the expected register.
However, certain patterns suggest a non-native English-speaking author or a template created by one. The phrasing can be overly stiff and unnatural. For example, the construction “Only applicants who provide written confirmation will be accommodated” is grammatically correct but excessively formal and verbose compared to more natural native phrasing. The style is a performance of “officialese” that captures the tone but occasionally misses the authentic rhythm and word choice of a genuine government document.
Forensic Linguistic Analysis
Forensic linguistics, which examines language for evidence, uncovers the sender’s true intent. The pragmatic function of the emails is directive and coercive. Every sentence works to compel the recipient to act: confirm attendance, make a phone call, or provide information. The discourse is structured as a problem-solution narrative, but with the sender fabricating the problem and positioning themselves as the sole provider of the solution.
The phrase “This is a courtesy communication and not a formal Office Action” is a masterful piece of linguistic manipulation. It frames the interaction as helpful, disarming the recipient’s defenses, while simultaneously introducing the implicit threat of a more severe, formal consequence should they fail to comply. The mixture of registers—the hyper-formal legal citations alongside informal emojis—is a strong indicator of inauthenticity. A genuine government agency maintains a consistent formal register and would not use such informal symbols in a notice threatening prosecution delays. The language constructs a facade of helpful authority to mask a coercive demand for contact and, ultimately, payment.
Operational Flow of the Fraud Scheme
The entire operation follows a predictable lifecycle, from target acquisition to financial extraction. The following Mermaid.
Assessment
The fraud scheme represents a significant and persistent threat to intellectual property applicants. The perpetrators’ success stems from their exploitation of a public information system and their deep understanding of the Applicant’s psychological state. They blend technical savvy with polished social engineering to create a highly effective deception. The vulnerability lies in the public availability of applicant contact data, a necessary component for transparency in the trademark system. Mitigation relies entirely on applicant awareness. All unsolicited communications claiming to be from the USPTO must be treated with extreme suspicion. Applicants must independently verify every notice by logging into the official TEAS portal or by consulting their legal counsel, never by using the contact information provided in a suspect email.
Samples
Dear Applicant,
Pursuant to 15 U.S.C. §§1051–1052 and TMEP §§806.01, 1401.02, and 1202, your trademark application is currently under classification review by the United States Patent and Trademark Office (USPTO). Preliminary examination indicates that additional or revised international classification(s) may be necessary to accurately reflect the scope of your goods or services under the Nice Agreement. Failure to comply may result in narrowed protection or prosecution delays.
Action Required
To prevent issuance of a formal Office Action, you are requested to participate in a classification consultation on:
Date: Monday, August 18, 2025
Time: 08:00 AM – 5:00 PM (ET)
Phone: (571) 771-3844 (Ext. 1)
Please note: Only applicants who provide written confirmation will be accommodated. Unscheduled or unsolicited calls will not be accepted.
Email Option
If a phone consultation is not feasible, you may respond in writing with:
A description of your business activity
A list of goods/services offered
Any relevant commercial use details
This written response will be reviewed in lieu of a phone consultation.
Required Acknowledgment (please reply with):
“I, [Full Legal Name], as the owner/Applicant of Trademark Serial No. [Serial Number], acknowledge receipt of this Classification Review Notice issued by the USPTO, and confirm my intent to participate in the consultation on August 18, 2025, or to respond in writing as instructed.
Failure to respond may result in classification deficiencies, delays, or narrowed protection.
Please reply with “Confirm” to participate.
Sincerely,
United States Patent and Trademark Office
U.S. Application Serial No.: ########
Mark:
ACME LLC
Dear Applicant,
We are writing to inform you that after reviewing your trademark application for ACME LLC, we have identified missing information that must be corrected before the application can proceed.
Identified Issue:
The application is missing a properly worded identification of goods/services, as well as the corresponding International Class number(s), in accordance with 37 C.F.R. § 2.32(a)(7)–(8) and TMEP §§ 1401–1402.
What You Need to Do:
To avoid delays or possible abandonment of your application, please take the following steps:
- Submit a revised identification of goods/services using USPTO-accepted language.
- Include the correct International Class number(s).
- Contact your assigned Examining Attorney, Mr. Michael Clark, for assistance.
📞 Michael Clark – (571) 771-0730
⏳ Preferred Contact Time: Before 6:00 PM PST today
We appreciate your prompt attention to this matter. If you need clarification or assistance, please don’t hesitate to reach out.
Sincerely,
Cynthia Tripi
Assistant to the Examining Attorney
U.S. Patent and Trademark Office
NOTE: This is a courtesy communication and not a formal Office Action. It is intended to help you resolve outstanding application issues in a timely manner and preserve your application status.





You must be logged in to post a comment.