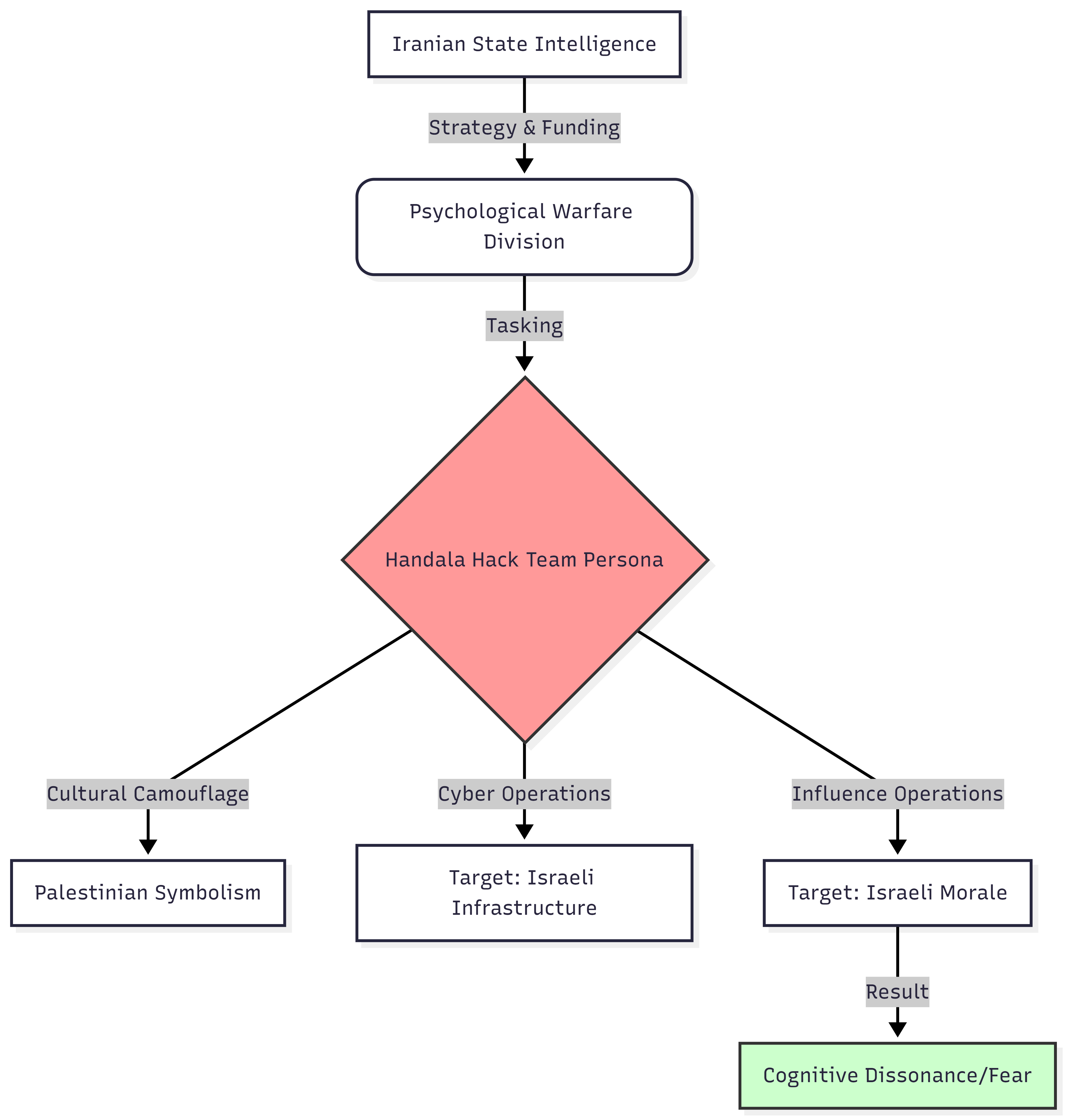
Tehran wears many masks. The “Handala Hack Team” represents one of the most deceptive. Analysts often mistake this group for a collective of skilled hackers. Intelligence assessment reveals a different reality. Handala operates as a psychological warfare unit. The group uses cyber intrusions as a stage for narrative manipulation. The recent “Bibi Gate” operation confirms this pattern. The objective remains clear: erode Israeli societal resilience through fear, not just code.
The Persona as a Weapon
The name “Handala” invokes a powerful symbol. Naji al-Ali created the character to represent Palestinian defiance. Iranian intelligence co-opted this icon. The Cultural Nexus framework exposes this theft. Tehran uses the Palestinian cause as a shield. The use of the Handala image grants the attackers a level of legitimacy among specific audiences. The persona masks the foreign state actor pulling the strings. Handala is not a grassroots movement. The group acts as a digital proxy for the Islamic Republic.
Anatomy of the “Bibi Gate” Operation
Handala claimed access to the phone of Tzachi Braverman, the Israeli Prime Minister’s chief of staff. The group dubbed the operation “Bibi Gate.” The announcement focused on fear. “We choose what you fear next,” they wrote. This statement reveals the true intent. The hack itself matters less than the anxiety it produces. The Adaptive Intelligence Lifecycle identifies this as a “Disrupt” phase action. The adversary does not need to release the data to win. The threat of release forces the target to react. Security services waste resources investigating the breach. Politicians worry about blackmail. The public loses faith in the security of their leaders.
Pattern of Deception
A trend analysis of Handala’s activity shows a reliance on “leak and shame” tactics. The group times its operations for maximum psychological impact. They struck on the anniversary of Hassan Nasrallah’s death. They targeted the “Saturday Files” to dominate the weekly news cycle. Technical sophistication remains low. The group relies on known vulnerabilities and phishing. The high volume of operations compensates for the lack of “Zero Day” exploits. The “Cyber Soldiers” of Iran rely on quantity to overwhelm the quality of Israeli defenses.
Visualizing the Proxy Relationship
The following chart illustrates the command and influence structure masking the Iranian state’s involvement.
Forensic Analysis of the Threat
Language used by Handala aligns with Iranian influence doctrine. Phrases like “psychological dominance” and specific threats against “inner circles” mirror IRGC (Islamic Revolutionary Guard Corps) rhetoric. Stylometric analysis links the group to the broader Iranian “RedWanted” campaigns. The coordination suggests a state-level directive. Handala functions as a megaphone for Tehran’s foreign policy. The group amplifies the narrative that Israel is unsafe, penetrated, and vulnerable.
Countering the Narrative
Defenders must look past the technical breach. The center of gravity for this threat lies in the mind of the victim. Hardening identity protections and securing personal devices stops the initial intrusion. Controlling the narrative stops the damage. Organizations must prepare for leaks as they prepare for fires. Silence and transparency kill the adversary’s momentum.
Reference Material
Treadstone 71 previously analyzed similar Iranian proxy activities. Review the Cybershafarat archives on Handala here.
The source analysis for this report comes from the ICT article: Bibi-Gate: Handala Hack Team – A Mask for Iranian Psychological Warfare.