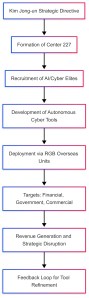
North Korea’s unveiling of Research Center 227 under the Reconnaissance General Bureau (RGB) represents more than the establishment of a new technical facility, signifying an evolution in the state’s strategic doctrine. The directive, reportedly issued by Kim Jong-un on March 9, 2025, initiates a focused push toward AI-powered offensive cyber operations. Located in Mangyongdae, outside the existing RGB command structure, the Center consolidates advanced cyber capabilities in an insulated node designed to scale and sustain continuous operations against adversarial cyber defenses.
The regime’s intent reflects a dual imperative- offensive cyber dominance and sovereign regime protection through asymmetric technological superiority. The chosen location near the political heart of Pyongyang underscores the perceived strategic importance. North Korea does not merely see cyber as a technical function. Cyber is a warfighting doctrine. The doctrine parallels the role of nuclear weapons—guaranteeing survivability and projecting power across domains where kinetic parity remains elusive.
Strategic foresight analysis provides a comprehensive lens for interpreting this initiative’s future trajectory. Using frameworks from Pherson Associates’ foresight doctrine, we can build a multi-factor model that decodes North Korea’s offensive cyber trajectory through six central pillars- intent, motivations, capabilities, functions, skill depth, and success probability.
INTENT- Centralized Command of Offensive Capabilities
The command to form Center 227 came directly from the supreme leader. That alone positions the endeavor not as opportunistic but as doctrinal. The purpose is not passive surveillance or defensive resilience. Rather, the goal is to create scalable systems capable of infiltrating and neutralizing adversary cyber defenses. The intent includes a shift from campaign-specific attacks to persistent capabilities that operate across time zones and infrastructures. The persistent capabilities are a desire to mimic aspects of Western nation-state tactics but on an AI-automated backbone.
MOTIVATIONS- Economic Survival and Strategic Signaling
The state’s dependency on sanctions-evasion mechanisms—particularly through cyberattacks targeting financial infrastructure—remains well documented. The development of AI-enhanced tools that automate information theft, conduct financial hacks, and mimic legitimate user behavior fulfills dual objectives. First, the program sustains economic lifelines through theft and fraud. Second, the program offers geopolitical signaling that North Korea, despite its isolation, retains strategic reach. This kind of reach-through-malice has proven more effective in shaping diplomatic conversations than formal negotiation tables.
CAPABILITIES- AI-Enhanced Disruption, Not Just Surveillance
North Korea is transitioning from spear-phishing and malware deployment to the engineering of fully automated systems that weaponize machine learning for information extraction, network compromise, and automated reconnaissance. The new Center’s core research objectives include breaking Western cyber defenses and deploying AI algorithms that accelerate malware customization, mimic network traffic and respond in real-time to incident detection systems.
FUNCTIONS- Centralized, Non-Deployed R&D Cell for Code Development
Center 227’s staff will not consist of forward-deployed cyber operators. Instead, the Center recruits elite graduates from Pyongyang’s top science and engineering institutions—many with doctorates in automation, algorithmic design, or advanced cryptography. Their task is not to “pull the trigger” but to engineer the guns and bullets. Tools developed will be handed off to deployed units under the RGB for international operations. This separation of R&D and operations enhances operational security and code modularity.
SKILL DEPTH- Structured, Elite, and Geopolitically Networked
Between 3,000 and 6,000 hackers work within the RGB or affiliated entities. Their training often begins in childhood and continues through elite university programs, some with support from Chinese, Russian, and Iranian institutions via clandestine exchange programs. North Korea’s education pipeline supports AI fluency and automation-centered architecture. While the command economy limits innovation, the state compensates through structure, discipline, and ideological indoctrination, which suppresses whistleblowing and enhances mission commitment.
LIKELIHOOD OF SUCCESS- High in Unregulated or Under-Defended Theaters
North Korean offensive operations exhibit proven success against poorly regulated crypto ecosystems, regional banks, decentralized finance platforms, and commercial networks without AI-based intrusion detection. AI-powered automation would exacerbate threat velocity, enable real-time obfuscation of attack vectors, and adapt malware behavior dynamically. Most Western defense postures lag in the proactive detection of AI-rewritten payloads and polymorphic behavior patterns. Center 227’s mission architecture directly targets this gap.
The model below illustrates North Korea’s likely operational arc using strategic foresight estimation-
Strategic Forecast
Three distinct scenarios define the strategic foresight trajectory over the next 36 months-
1. Operational Maturity (Most Likely, High Impact)-
Research Center 227 produces AI tools embedded with NLP-capable malware, self-replicating bots, and crypto-targeting automation. These tools facilitate ongoing financial attacks, disrupt Western supply chains, and remain undetected due to adaptive signatures.
2. Tactical Disruption (Moderate Probability, Medium Impact)-
AI tools malfunction or are intercepted mid-development due to insider betrayal or external sabotage. Operations slow. International attribution triggers targeted sanctions or sabotage.
3. Escalation Spiral (Low Probability, Catastrophic Impact)-
Offensive capabilities cross a red line—e.g., power grid disruptions, hospital shutdowns, or military intrusions. Western states respond with retaliatory cyber strikes or covert action.
The establishment of Research Center 227 reflects North Korea’s full integration of cyber as a strategic pillar alongside nuclear and missile forces. The use of AI to automate and amplify offensive operations represents a high-threat evolution in the regime’s asymmetric strategy. The Center’s isolation from active operators enhances deniability, modular design, and adaptability.
The success of the Center will depend on how swiftly adversarial states move to harden defenses against adaptive malware, AI-directed penetration tools, and persistent reconnaissance systems. Failure to respond with equivalent innovation will cede ground to an actor unconstrained by economic rules, ethical boundaries, or strategic inertia. North Korea’s cyber doctrine is not emergent. The doctrine is declared, resourced, and accelerating. Silence ensures surprise. Inaction guarantees impact.




You must be logged in to post a comment.