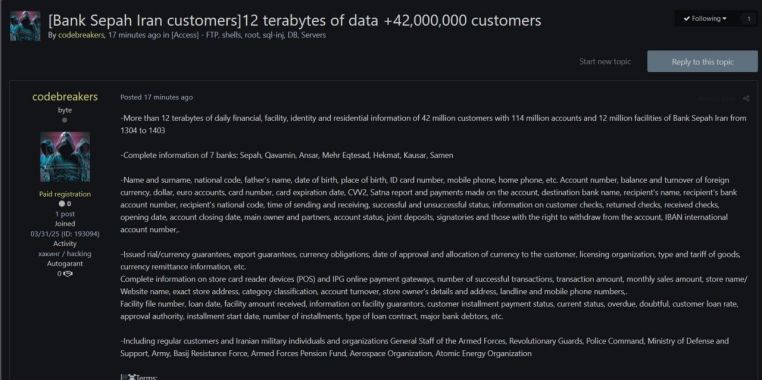
Iran’s cyber vulnerabilities, authoritarian overreach, and corruption-laden banking system have again been laid bare. Codebreakers Group’s announcement confirms that Bank Sepah—one of Iran’s oldest and most influential financial institutions—has been gutted. Over 12 terabytes of sensitive customer data tied to 42 million individuals, 114 million accounts, and 12 million registered facilities were stolen and placed up for sale. Iran’s digital defenses failed catastrophically, compromising national financial infrastructure and exposing both civilian and military clientele to espionage, fraud, and extortion. The scope of the compromise obliterates any claim by the Islamic Republic to sovereignty over its own data space.
The breach includes granular identity and transactional details: national codes, names, birth dates, addresses, phone numbers, card data, account numbers, balances, currencies, check information, and transaction metadata. For over a decade—between 1304 to 1403 in the Iranian calendar—the entire financial history of Iran’s population was siphoned into the hands of a cybercrime group operating in broad daylight on exploit.in. Data from seven banks were included: Sepah, Qavamin, Ansar, Mehr Eqtesad, Hekmat, Kausar, and Samen. Collectively, they form the primary backbone of Iran’s militarized and state-controlled financial system. These banks process funds for the Islamic Revolutionary Guard Corps (IRGC), the Ministry of Defense, the Atomic Energy Organization, and military-linked pension schemes. In short, the IRGC’s payroll just got indexed for global sale.
The fallout will not be limited to financial fraud or identity theft. The leak exposes IRGC officers, nuclear technicians, aerospace engineers, Qods Force operatives, Basij commanders, police officials, and defense procurement managers. Their full financial trails—IPG gateway usage, store addresses, device IDs, installment plans, joint signatories, and suspicious checks—now sit in hacker forums waiting to be analyzed. Any intelligence agency, private contractor, or regime dissident with enough cryptocurrency can now unmask the regime’s operational hierarchy through raw transaction mapping.
This breach demonstrates not simply cyber negligence but systemic rot. Iranian banking IT infrastructures remain underfunded, unsupervised, and riddled with obsolete architecture, many still depending on 20th-century mainframes and brittle SQL-based data lakes. Sepah’s networks, many of them air-gapped only in name, show no evidence of proper segmentation or encryption-at-rest protocols. Even the fact that 12 terabytes were extracted indicates a total absence of detection, throttling, or mitigation mechanisms. Iran’s propaganda machine obsessively promotes sovereignty, yet cannot defend its citizens’ data from being auctioned in hacker bazaars.
The Islamic Republic demands its citizens sacrifice privacy, liberty, and economic freedom under the banner of national resistance, yet stores that very personal data in cracked silos built by incompetent contractors tied to regime elites. That data is now permanently beyond the regime’s control. Financial histories that could destroy marriages, expose embezzlement, and link terrorist financing to state-backed banks are now permanently outside Tehran’s reach. The regime’s own surveillance state has become a liability.
Sepah, the same institution funding oppressive crackdowns, military procurement, and ideological indoctrination programs, now finds itself the greatest vector for foreign manipulation. Every dissident, smuggler, soldier, and supporter using Sepah’s services has been mapped. The regime, in seeking to dominate and exploit its citizens through financial control, has exposed itself to total financial penetration by hostile states, rival factions, and black-market brokers. A government obsessed with controlling information has now lost the one type it valued most: transaction metadata.





You must be logged in to post a comment.